Anomaly Detection
Guide to using Anomaly Detection log streaming to alert unusual behaviors across your workspaces.
Overview
If you're interested in using this feature, please reach out to your Customer Success Manager or Account Executive.
Anomaly events allow you to be alerted to unusual behavior across your workflows within the log stream events. Supporting this are two event types, anomaly and rule based.
Anomaly Events
Anomaly events use trends from your organization to automatically alert of unusual task volumes and task errors within your workflows. These events provide key signal alerting users to unusual behaviors, while adapting and scaling to new workflow contexts. They are:
- Behavior-aware: Alerts are derived from your organization’s historical data and adapt to evolving usage patterns.
- Pattern-based: The system reduces false positives for workflows with legitimate variability - such as normal processing spikes, event-driven patterns with quiet periods, or different behaviors at different times. You control the algorithm sensitivity, allowing detection to recognize real patterns including high-load periods as normal while catching genuinely unusual behavior.
- Multi-timescale: Anomalies are evaluated over 5-minute, hourly, and daily intervals for fine-grained insight.
- Contextual: The system learns regular behavior by hour of day, day of week, and day of month. If no specific trend is found, it falls back to a global configurable baseline.
- Workflow-specific: Anomaly events are generated per workflow, helping you isolate and investigate issues precisely. Please note the rule-based applies to the whole org.
Rule Based Events
Rule-based anomaly events are for deterministic monitoring. Users can set custom thresholds to monitor task behavior across your organization. For example by setting the maximum number of tasks per organization over the last 30 days you will receive an event when tasks exceed the predefined threshold.
How to Get Started
Please note to have access to Anomaly Events you must have log streaming enabled, please see log streaming detail page for more information. To view these events, please contact your admin to set up the Anomaly Detection in your organization account settings. Under account settings you can adjust:
- Enabling the Rule based event and its settings.
- Anomaly based statistical settings and its settings.
- Event payload details are provided below.
- Example dashboard to visualize the events in your monitoring platform are provided below.
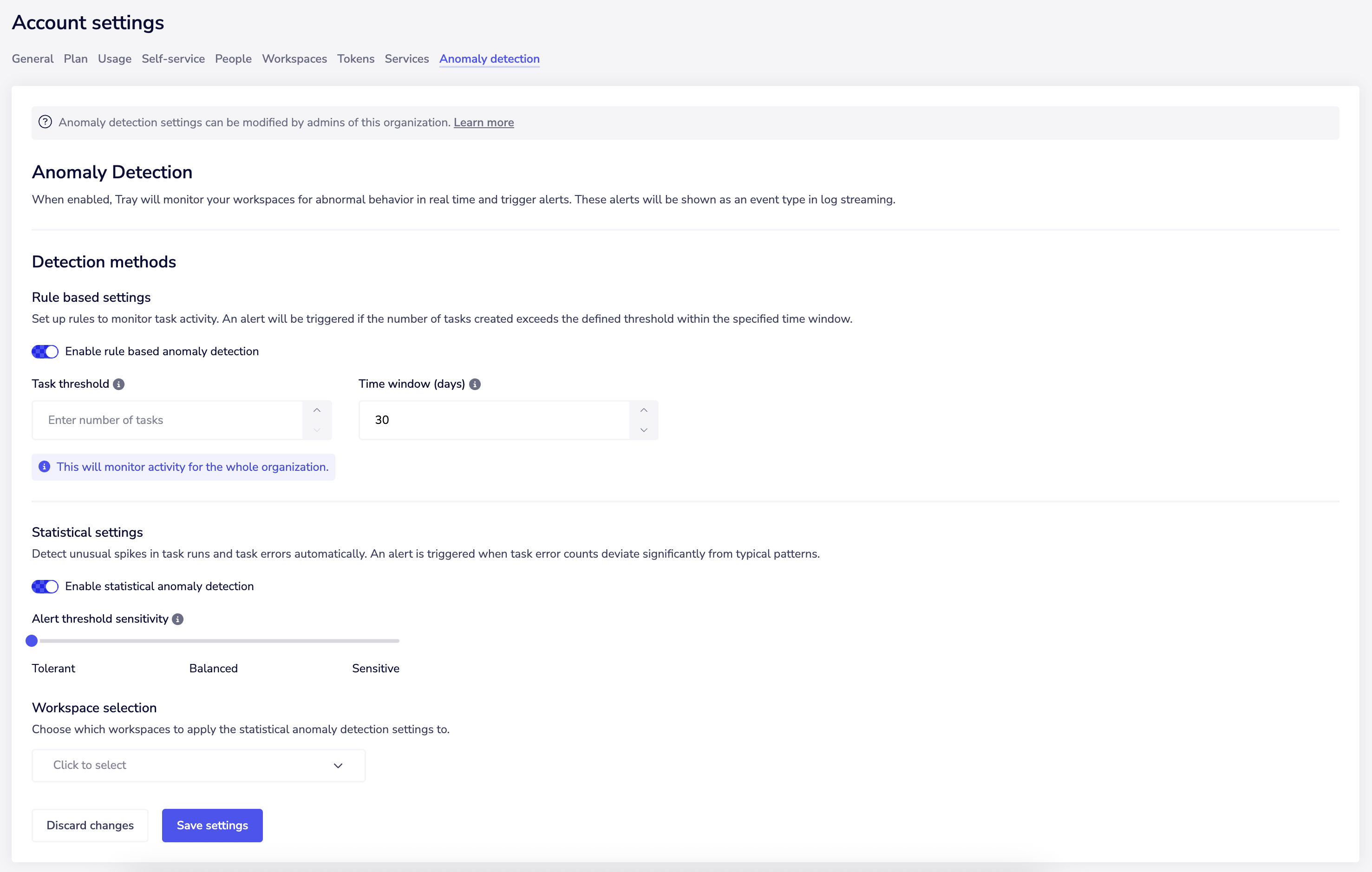
What alert threshold should I use?
We automatically calculate your typical usage pattern and flag anything that deviates significantly from normal. The alert threshold sensitivity determines how far from normal something needs to be before triggering an alert. We recommend setting it to balanced and reviewing after one week to assess the quality of alerts and adjusting accordingly.
Example Events
For anomaly events:
Anomaly detected:
Organization_id: string
Workspace_id: string
Workflow_id: string
Timestamp: 2025-05-29 09:45:00
Current Metrics:
{
"5-min": {
"num_tasks": 1166,
"failure_rate": 0.0
}
}
Anomaly Results:
Time Range: 5-min
Anomaly: True
Confidence Level: high
Thresholds:
Seasonal Task Upper Bound: 531
Seasonal Task Lower Bound: 0
Seasonal Failure Rate Upper Bound: 0.007831641083109356
Seasonal Failure Rate Lower Bound: 0.0
Threshold Confidence: high
Used Pattern: thresholds:string:5-min:global
For the rule-based anomaly events:
Anomaly detected:
Organization_id: string
total_tasks: int
lookbackDays: int
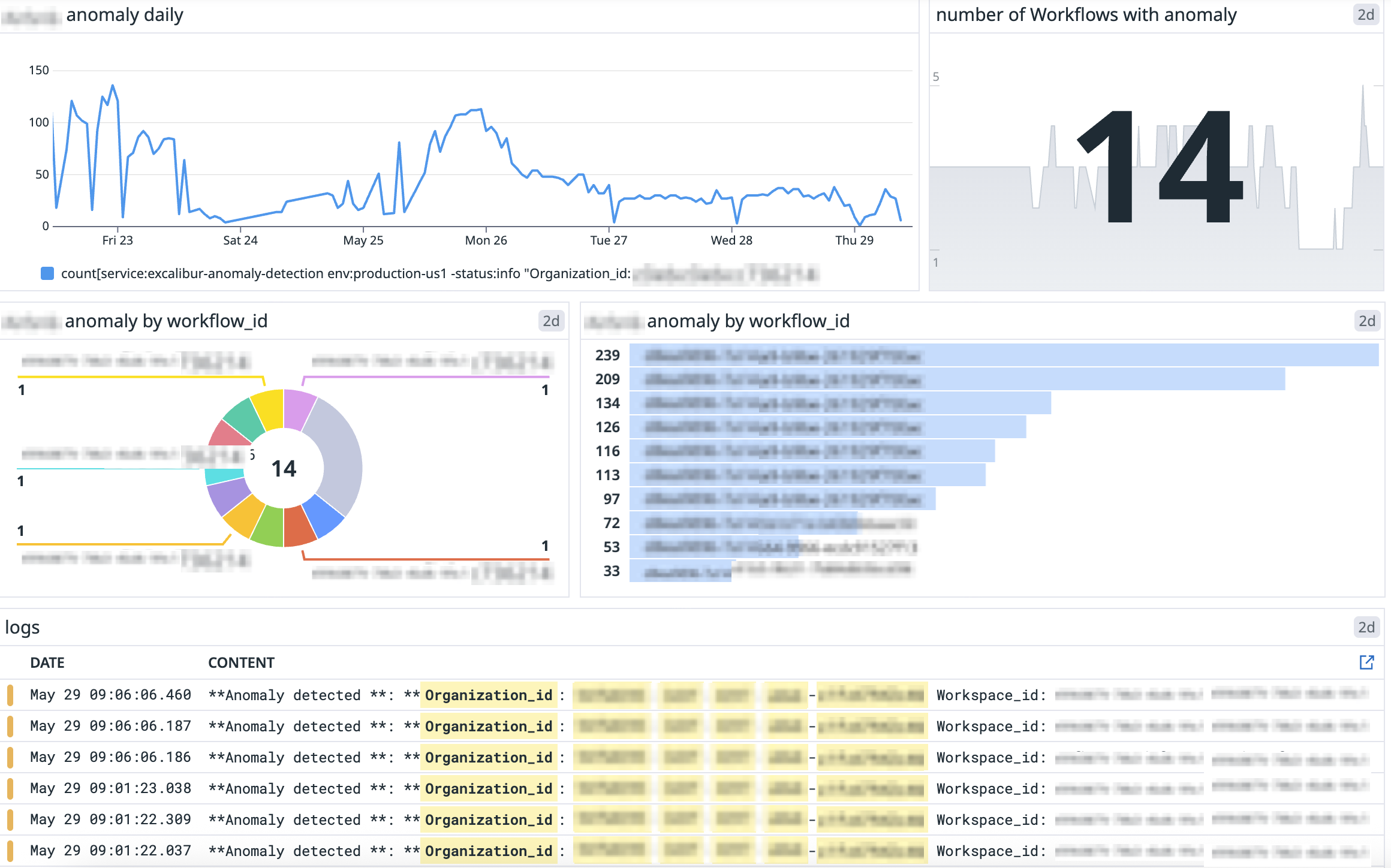
Visualizing events in your monitoring platform
Within your external systems as a minimum we recommend:
- Visualizing the events per time period in a time series
- Aggregating the number of events generated per workflow
- Aggregating the number of workflows with events
Please see an example dashboard that shows anomaly detection events below: